|
Documentation Contents | User Documentation | Administrator Documentation | Index of terms | Technical Support | On-line Search |
| Security questions on WCfO and other WAP applications |
This document will answer your questions about WAP and WCfO security.
WAP security is different for the connection you are using:
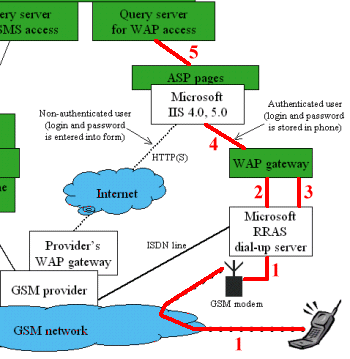 If you're using private dial-up server and a private WAP gateway, you're getting the best
security.
If you're using private dial-up server and a private WAP gateway, you're getting the best
security.
(We assume that dial-up server is in your private network or (better) in the demilitarised zone between internal and a external firewall. Also, all of following text is based on usage of Microsoft RRAS as a dial-up server.)
Communication description (and hints)
Phone authenticates itself to dial-up server by using standard PPP authentication protocols (CHAP, PAP...). Some of them are secured - so password is sent encrypted from mobile phone to dial-up server. Almost all of mobile phones can use secured PPP login protocols.
You may use standard Windows NT tools to configure RRAS (dial-up) parameters, so only some of users can dial to RRAS server, or they can only log-in in selected hours during a day and so on.
Logged user can access all of the Windows NT network by default. But you can reconfigure RRAS to be more secured: you can set, that dial-up users can access only the computer where RRAS is running. WAP gateway then must be running on the same computer, of course. (Or - better - you can put your dial-up server to demilitarised zone).
Security warning: You can switch on logging of RRAS server. This is described in Microsoft KB record Q161426. Then all of data sent throught RRAS, including password if sent unencrypted, may be logged into WinNT/Tracing/ directory.
Request and response data are sent unencrypted. If you'll switch on logging on WAP gateway and set loging level to greater value than 5, you'll see content of all data packets sent.
Also, all of parameters sent to WWW server may be logged by WWW server. By default, parameter logging is switched off.
ASP pages communicate with Query Server throught COM interface - directly. Query server then access MS Exchange Server using CDO and MAPI interfaces. Data from that interfaces may probably be sniffed out from network, but they may be encrypted. Data processed in Query Server may be logged to disk if you switch on logging.
If you want to get security as high as possible, we recommend to:
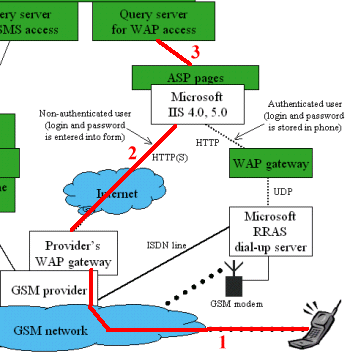 Using of GSM provider's WAP gateway is cheap, but not really secure. You may increase the security
by special settings, but the correct way is to use your onw dial-up server and
WAP gateway.
Communication description (and hints)
Using of GSM provider's WAP gateway is cheap, but not really secure. You may increase the security
by special settings, but the correct way is to use your onw dial-up server and
WAP gateway.
Communication description (and hints)
All of your data may be logged somewhere in provider's site.
If your GSM provider support encrypted WAP connection, it is much better. No data can be logged on provider's systems. But many of GSM providers doesn't support encrypted communication on their public WAP gateways.
There is no authentication sent from provider's WAP gateway to your WWW server. So WAP application query user for authentication by sending a standard form "Enter username and password" to be filled. This is discomfortable.
If you're not using secure (SSL - HTTPS) communication (not supported by WAP gateway often - as described in point 1), all of your data, including NT username and password, are sent unencrypted, so they may be tapped and abused.
WWW server may write all of parameters into logfiles - including username and password. By default, parameter logging is switched off on IIS.
And as a last trouble, your WWW server have to be accessible from internet. So you have to secure it - apply all of latest patches, service packs and so on.
Query server then access MS Exchange Server using CDO and MAPI interfaces. Data from that interfaces may probably be sniffed out from network, but they may be encrypted. Data processed in Query Server may be logged to disk if you switch on logging. Password isn't stored into log files at all.
If you want to get security as high as possible, we recommend to: